Active Threats
The Active Threats section of the Cyberguard Dashboard in the WP500 Gateway provides users with a detailed view of ongoing security threats that have been detected but not yet resolved. This section is designed to help users manage active threats by acknowledging and addressing them in a timely manner.
Monitor active threats
Follow these steps for Monitor Active threats.
- Click on the CyberGuard > Active Threat menu in the WP500 web interface.
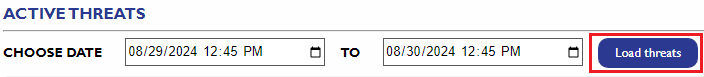
- Choose the start and end dates to filter threats for a specific time range.
- Click the Load Threat button to retrieve and display active threats for the selected time range.
- The active threats will be displayed on the screen, showing critical information about potential security risks detected by the system.
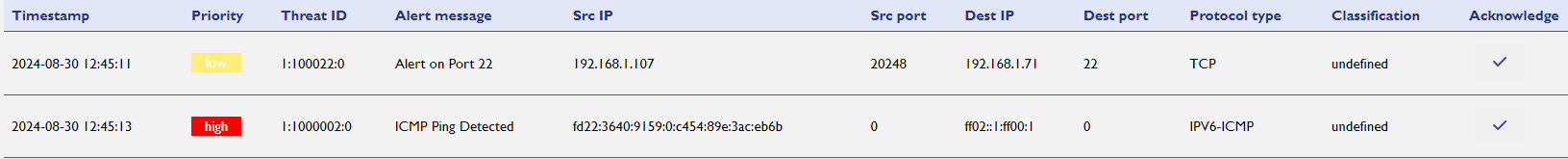
Active Threat Display:
The Active Threats section presents the threat information in a tabular format, making it easy for users to assess and manage each active threat. The table includes several key columns that provide detailed information about each threat:
|
Field |
Description |
|
Timestamp |
The exact time when the threat was generated, providing a timeline for when the incident occurred. |
|
Priority |
The threat's assigned priority level (e.g., Low, Medium, High), indicating the potential risk it poses to the system. |
|
Threat ID |
A unique identifier assigned to each detected threat for easy reference and tracking. |
|
Alert Message |
A description of the threat, providing additional context or details about the nature of the security risk. |
|
Source IP |
The IP address from which the detected threat originated. |
|
Source Port |
The port number associated with the source from which the threat was initiated |
|
Destination IP |
The target IP address that the threat is attempting to compromise or impact. |
|
Destination Port |
The port number associated with the destination |
|
Protocol |
The type of network protocol used in the threat, such as TCP, IPv6, or others. |
|
Acknowledge |
A button that allows users to acknowledge the threat, marking it as reviewed or addressed. |
Acknowledge Threat:
Each active threat listed in the table includes an Acknowledge button. This feature is designed to streamline threat management by allowing users to mark threats as acknowledged, indicating that they have been reviewed and are in the process of being addressed.
- The Acknowledge button is provided for each active threat in the table, giving users the option to quickly mark a threat as acknowledged once it has been reviewed.
- When the Acknowledge button is clicked for a specific threat:
- The threat is marked as acknowledged in the system, indicating that it has been identified and reviewed by the user or system administrator.
- The threat moved to the Threat Log in the Cyberguard section, helping users to track which threats have been dealt with and which ones still require attention.