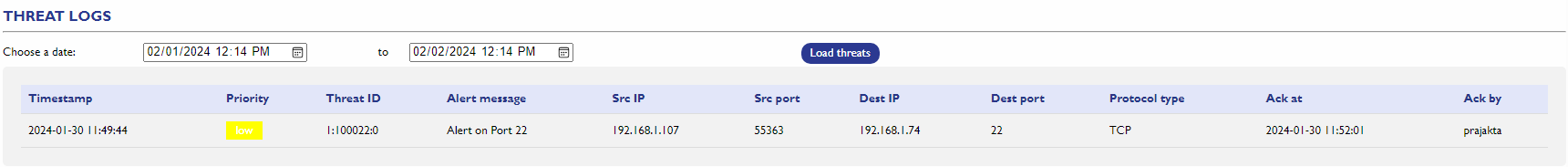
Threat Log
The Threat Log in Cyburguard provides a detailed record of all detected threats, offering valuable insights into the nature, priority, and context of each incident. This log includes essential information such as Threat Type, Threat Priority, Timestamp, Destination IP, Destination Port, Source IP, and Source Port Number. Understanding and analyzing this information is crucial for proactive threat management and system security.
Threat Type: Identifies the specific category or nature of the threat. Threat types may include malware, phishing attempts, suspicious network activity, or other security-related events.
Threat Priority: Categorizes the severity level of each threat. Prioritization helps users focus on addressing the most critical issues promptly. Threat priorities are typically classified as Low, Medium, or High.
Timestamp: Records the date and time when the threat was detected. This timestamp is essential for tracking the timeline of security events, aiding in forensic analysis and incident response.
Destination IP: Displays the IP address of the system or network entity that is the target of the threat. Understanding the destination helps in assessing the potential impact on critical assets.
Destination Port: Specifies the port number on the destination system where the threat is targeted. Port information is crucial for identifying the specific services or applications that may be vulnerable.
Source IP: Indicates the IP address of the origin or source of the threat. This information is vital for tracing the potential source of an attack and implementing necessary preventive measures.
Source Port Number: Represents the port on the source system from which the threat originates. Analyzing the source port helps in understanding the nature of the threat and its potential methods of infiltration.
Logs of threats is shown in the table.
Procedure to Check Threat Logs
- Choose From and To Date:
On the Cyburguard Dashboard, locate the "Threat Log" section
Look for date selection fields labeled "From Date" and "To Date."
Click on each field to access the calendar or input a specific date range manually.
Choose the starting date in the "From Date" field and the ending date in the "To Date" field.
- Click on Load Threats Button:
After selecting the desired date range, locate the "Load Threats" button.
Click on the "Load Threats" button to initiate the retrieval of threat logs within the specified date range.
Cyburguard will process the request and fetch the relevant threat log data based on the chosen timeframe.
- View Threat Logs:
The log entries will include information such as Threat Type, Threat Priority, Timestamp, Destination IP, Destination Port, Source IP, and Source Port Number.
Review the threat logs to gain insights into the security events during the specified timeframe.
Created with the Personal Edition of HelpNDoc: Effortlessly Create Professional Documentation with HelpNDoc's Clean UI