Active Threats
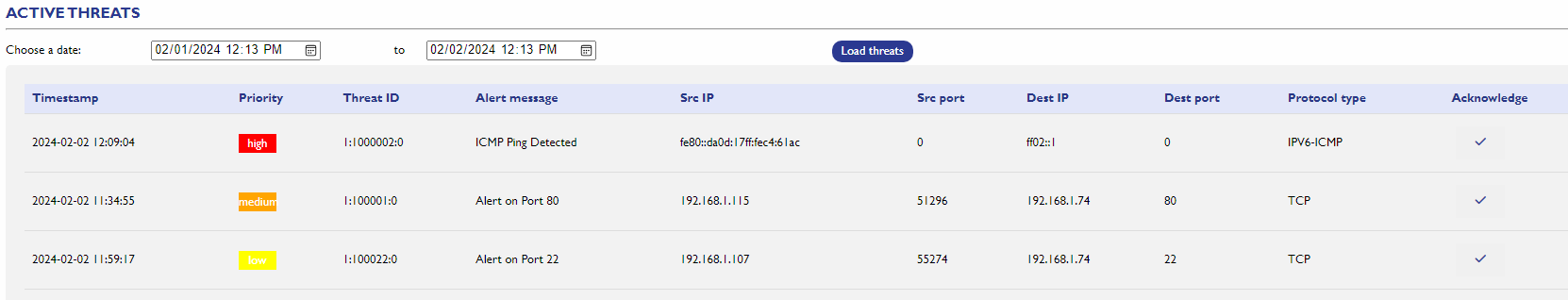
Active Threats Section
Table Display:
Displayed Data: Active threats information is presented in a table.
Columns: The table includes relevant columns such as Threat ID, Source IP, Destination IP, Threat Type, Priority, etc.
Acknowledge Button:
Functionality: Acknowledge button is provided for each active threat.
Action: By clicking on the "Acknowledge" button for a specific threat:
The threat is marked as acknowledged.
The threat may be moved to the acknowledged threats count in the overview section.
Created with the Personal Edition of HelpNDoc: Produce Kindle eBooks easily