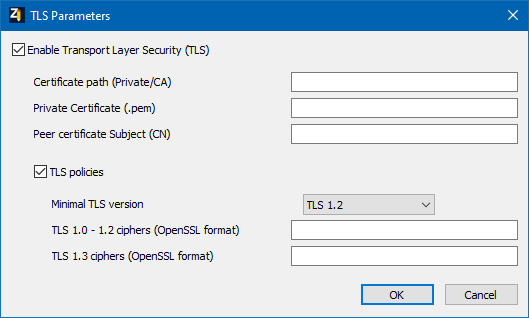
TLS Parameters
TLS settings
|
Parameter |
Description |
|
Enable Transport Layer Security (TLS) |
Checkbox for activation of secured communication to destination. Default: inactive |
|
Certificates path (Private/CA) |
Storage path for certificates on the target system. An absolute or relative path can be configured. The configured path must contain 2 subdirectories CA and PRIVATE.
Example: ./PKI |
|
Private Certificate (.pem) |
Filename of the private certificate. |
|
Peer certificate Subject (CN) |
Optional Common Name of the peer certificate. When configured, only a connection with a communication partner is established that uses a certificate from a trusted CA with the specified Common Name. |
TLS policies
The settings of this option group are only available if the options Enable Transport Layer Security (TLS) and TLS policies are active.
|
Parameter |
Description |
|
Minimal TLS version |
Minimum TLS version, used for the secured communication. A TLS version should be selected that is supported by both communication partners. Higher versions offer better security. The internal default maximum TLS version is set at TLS 1.2, except when TLS 1.3 is configured as minimum TLS version. Selection from a drop-down list:
Default: TLS 1.2 |
|
TLS 1.0 - 1.2 ciphers (OpenSSL format) |
List of supported ciphers, separated with ":" Default: empty With the default empty value, all relevant and secure ciphers are supported, depending on the selected TLS version. Only available if the configured Minimal TLS version is not TLS 1.3. Example: ECDH-RSA-AES128-SHA256:AES256-SHA256 |
|
TLS 1.3 ciphers (OpenSSL format) |
Enumeration of supported cipher suites with TLS version 1.3. Default: empty With the default empty value, all TLSv1.3 cipher suites are supported. Example: TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256 |
§§ Splitter
Close dialog
|
Option |
Description |
|
OK |
Applies settings and closes the dialog. |
|
Cancel |
Discards all changes and closes the dialog. |
TLS Parameters |
|
IEC 61131-3 Automation platform > Drivers - Fieldbus configuration > MODBUS Master > Fieldbus configuration > Settings in the fieldbus dialogs > Master/port configuration > TLS Parameters |
Created with the Personal Edition of HelpNDoc: HelpNDoc's Project Analyzer: Incredible documentation assistant