Network Security
Firewall Configuration
The WP 500 incorporates a powerful firewall as a cornerstone of its defense-in-depth strategy, providing robust protection against unauthorized access, malicious activities, and potential security threats. This section outlines the significance of the firewall in securing the WP 500 and its role in maintaining a resilient security posture.
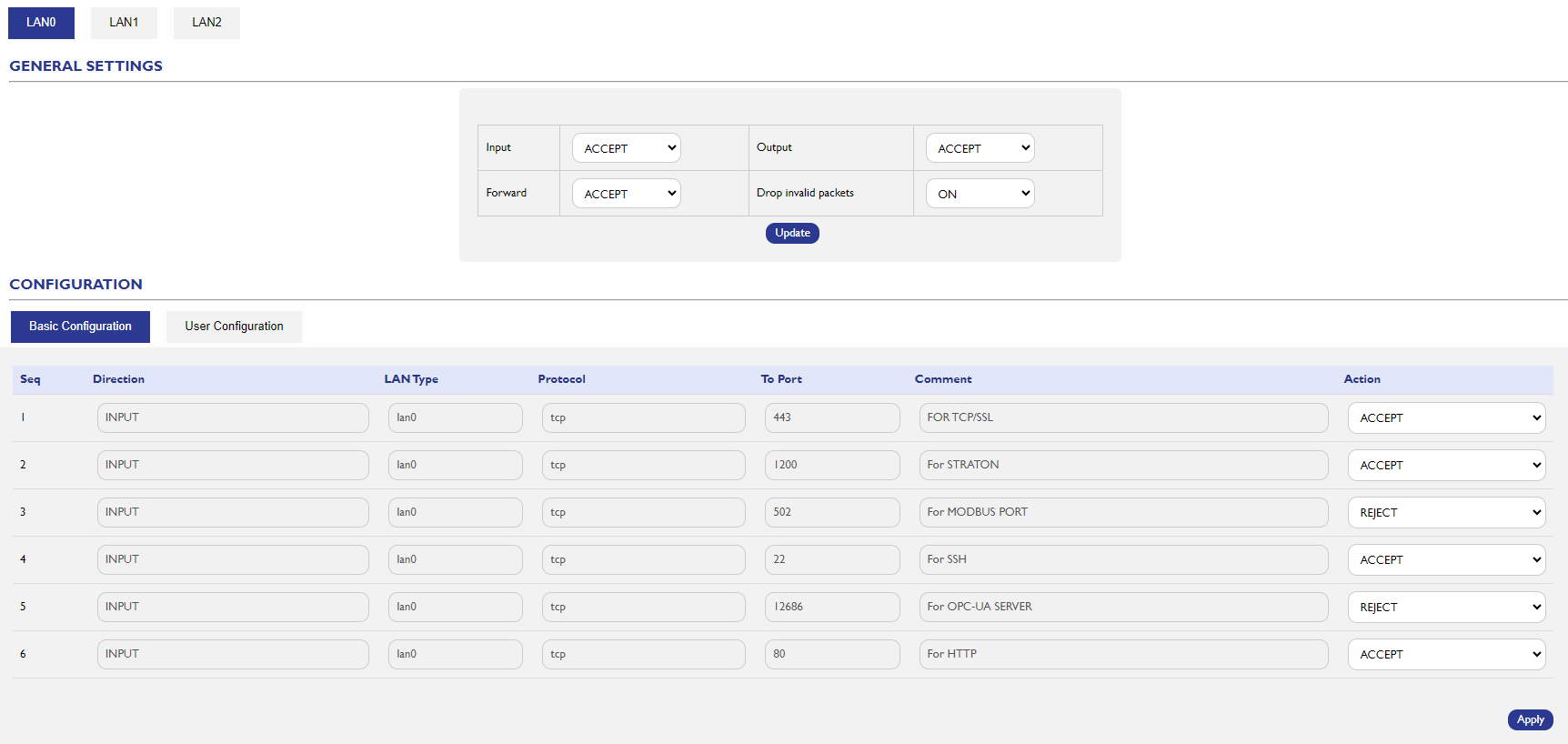
Traffic Rules with IP Tables:
- The WP500 allows users to implement traffic rules using IP Tables. This feature enables fine-grained control over incoming and outgoing network traffic for each network interface.
- Users are advised to configure these rules appropriately for each interface, tailoring the settings to their specific operational needs and security requirements.
Network Segmentation
- Network segmentation is a critical practice for enhancing security. The WP500 supports this with multiple LAN interfaces:
- LAN0 Interface: Recommended for external network connectivity, such as internet access. This separation helps in mitigating the risk of external attacks.
- LAN1 Interface: Designated for communication with IO modules. This isolation ensures secure and uninterrupted internal communication.
- LAN2 Interface: Advised for use with third-party networks, enabling secure interactions with external systems while keeping core operations segregated.
Intrusion Detection & Prevention:
- The IDS passively monitors network traffic, analyzing packets for suspicious patterns or anomalies.
- Utilizes a database of known attack signatures to identify and alert on recognized patterns associated with common threats.
- Unlike IDS, IPS takes immediate action to block or prevent identified threats in real-time.
- Adjusts firewall rules dynamically to block malicious traffic based on the identified threats.
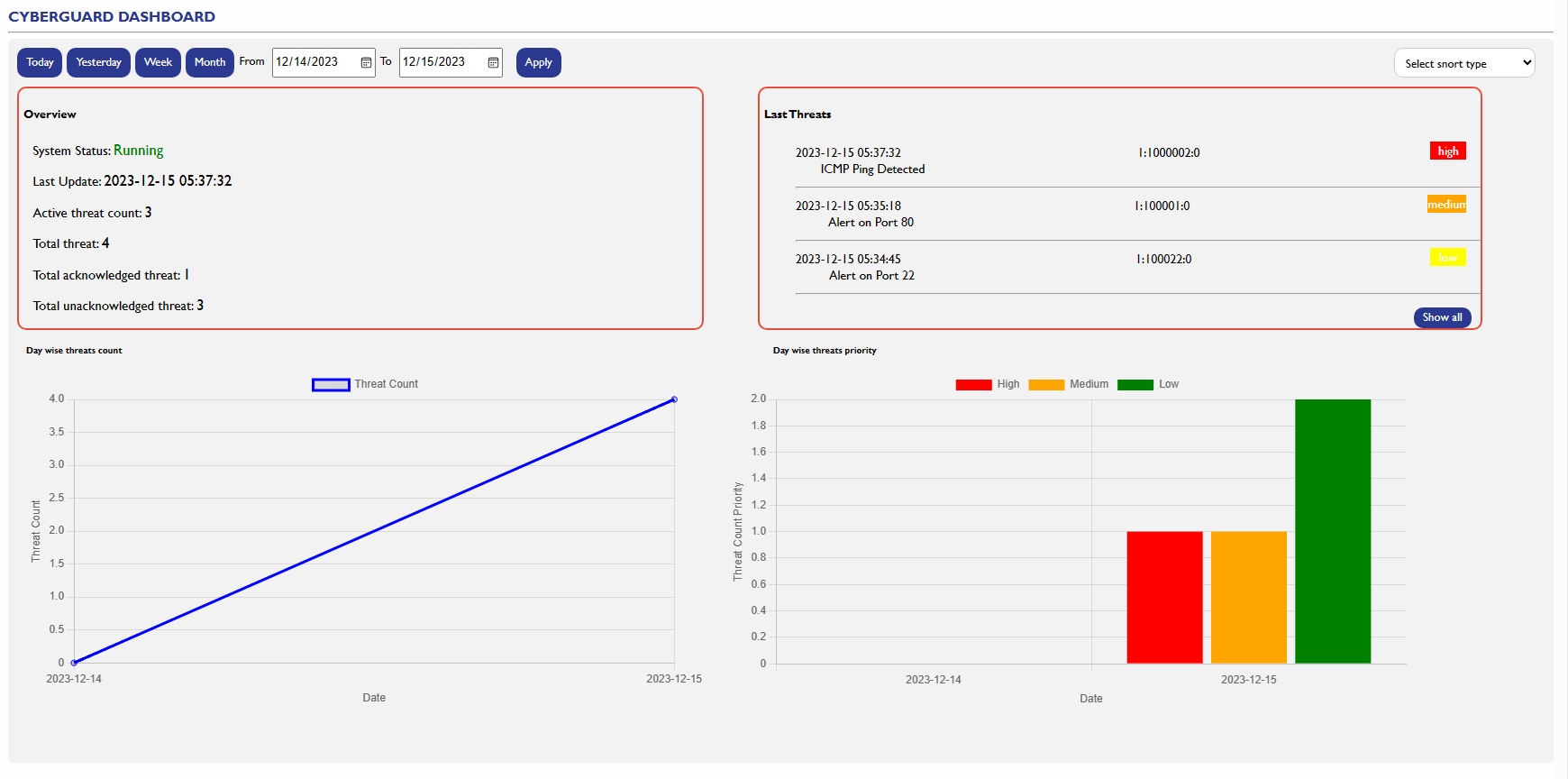 The Cyber Guard dashboard is your central hub for monitoring and managing the security status of your system.
The Cyber Guard dashboard is your central hub for monitoring and managing the security status of your system.
1. System Status:
- Indicates whether the Cyber Guard system is currently running or stopped.
- Ensures users are immediately aware of the operational status of the system.
2. Last Update Date:
- Displays the date and time of the last system update.
- Provides transparency on when the system was last updated, helping users stay informed about the currency of their security configurations.
3. Number of Active Threats:
- Presents the real-time count of active threats currently detected by Cyber Guard.
- Allows users to assess the current threat landscape and respond promptly to emerging security risks.
4. Number of Acknowledged Threats:
- Indicates the total count of threats that have been acknowledged by system administrators or users.
- Offers insights into the proactive management of recognized threats, showcasing the organization's response efficacy.
5. Number of Unacknowledged Threats:
- Reflects the count of threats that have been detected but have not yet been acknowledged or addressed.
Created with the Personal Edition of HelpNDoc: Full-featured Kindle eBooks generator