Network Security
The WP500 incorporates a comprehensive set of security features, including a powerful firewall, intrusion detection and prevention systems, and network segmentation capabilities. These security measures are critical in defending the system against unauthorized access, malicious activities, and potential threats. This section provides an overview of the key network security configurations for the WP500 and best practices to maintain a resilient security posture.
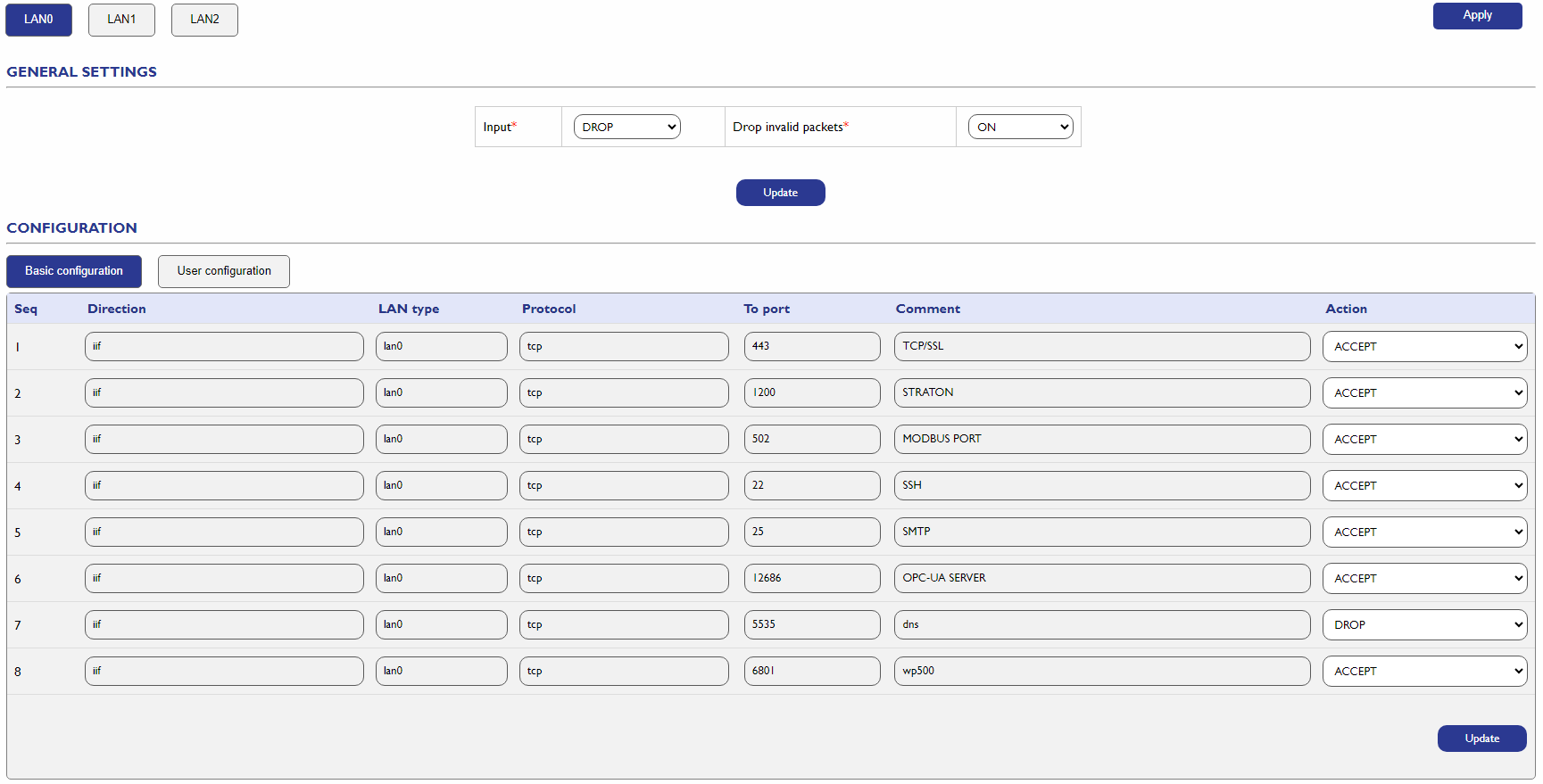
1. Firewall Configuration
The firewall is the cornerstone of WP500's security, acting as the first line of defense against unauthorized network traffic. Proper configuration of the firewall ensures that only legitimate traffic is allowed while blocking malicious activities.
Traffic Rules with IP Tables:
- WP500 allows users to define traffic rules using IP Tables for precise control over incoming and outgoing network traffic.
- Users can configure rules specific to each network interface, tailoring the settings to their operational needs and security requirements.
- This flexibility helps in defining policies that align with organizational security standards.
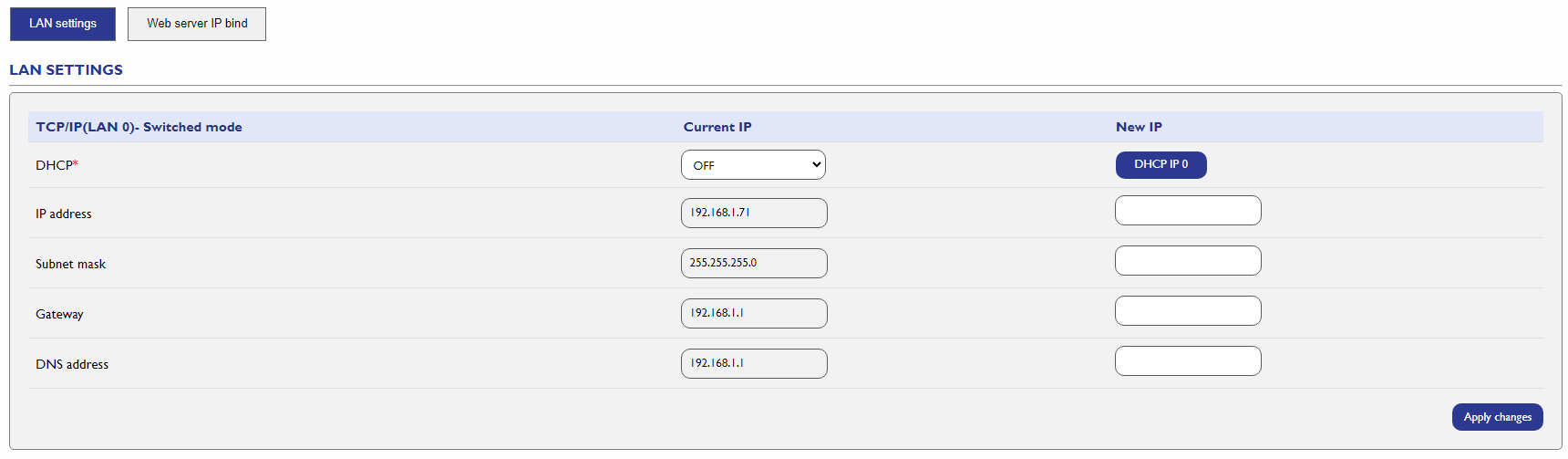
2. Network Segmentation
Network segmentation is a critical practice to limit potential attack surfaces and protect internal communications. The WP500 supports network segmentation with multiple LAN interfaces, allowing for the isolation of network traffic.
|
Fields |
Description |
|
LAN0 Interface |
|
|
LAN1 Interface |
|
|
LAN2 Interface |
|
3. Intrusion Detection and Prevention System (IDS/IPS)
The WP500's Intrusion Detection System (IDS) and Intrusion Prevention System (IPS) offer advanced threat detection and response capabilities.
|
Fields |
Description |
|
Intrusion Detection System (IDS) |
|
|
Intrusion Prevention System (IPS) |
|
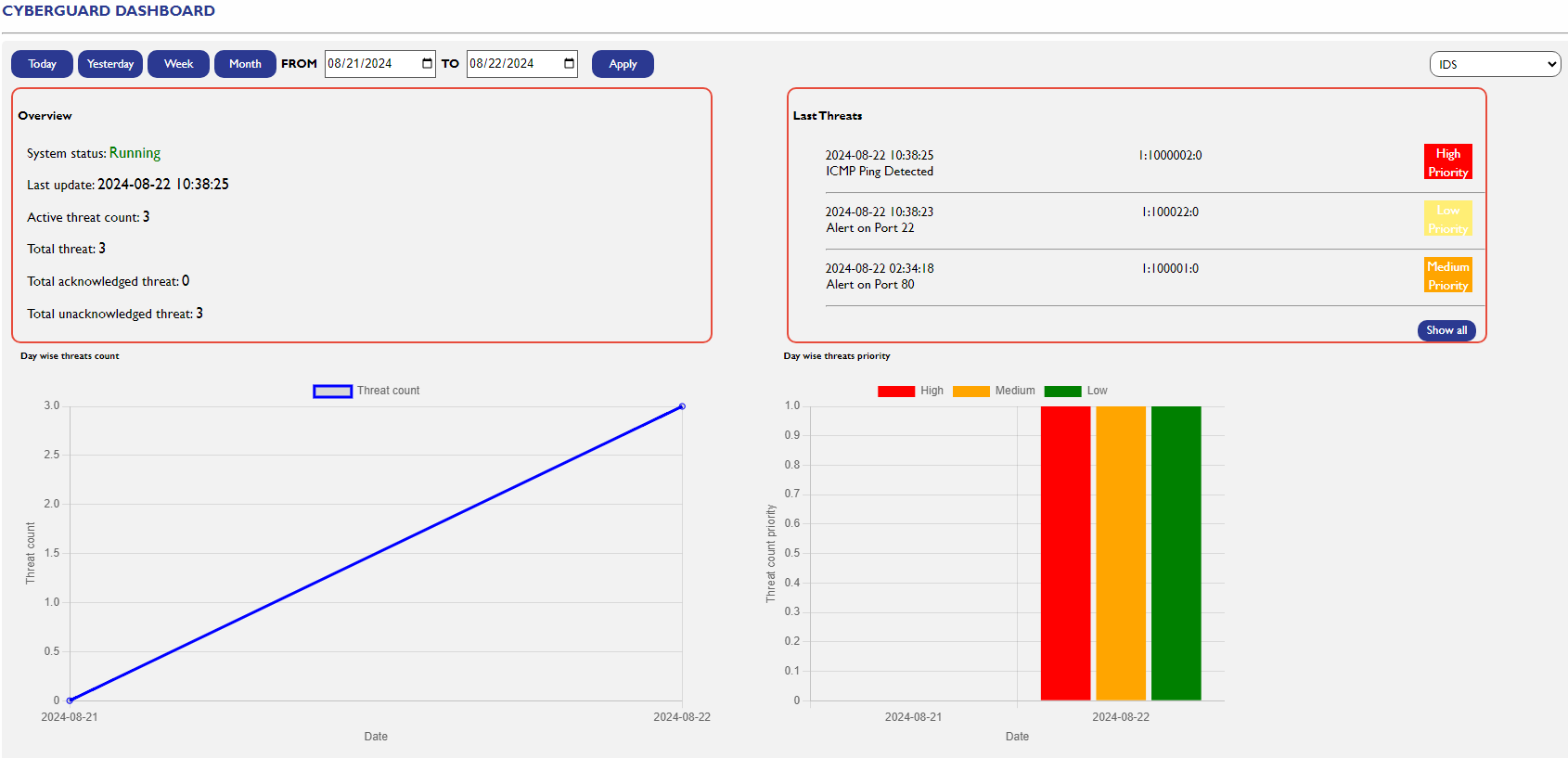
4. Cyber Guard Dashboard
The Cyber Guard Dashboard is the central hub for monitoring and managing the security status of your system. It provides real-time insights into the system's security posture and enables users to respond promptly to threats.
|
Fields |
Description |
|
System Status |
Indicates whether the Cyber Guard system is running or stopped, ensuring users are aware of the operational status. |
|
Last Update Date |
Displays the date and time of the last system update, keeping users informed about the currency of their security configurations. |
|
Number of Active Threats |
Shows the real-time count of active threats currently detected by Cyber Guard, allowing for immediate assessment of the threat landscape. |
|
Number of Acknowledged Threats |
Reflects the total count of threats that have been acknowledged by system administrators or users, demonstrating proactive threat management. |
|
Number of Unacknowledged Threats |
Indicates the count of threats that have been detected but not yet acknowledged or addressed, helping users prioritize and manage security tasks. |
Best Practices for Network Security:
- Regularly review and update firewall rules and traffic policies to ensure they align with evolving security requirements.
- Implement network segmentation to reduce the risk of lateral movement by attackers.
- Monitor the Cyber Guard Dashboard regularly to stay informed of potential threats and system status.
- Utilize the IDS/IPS features to detect and respond to threats in real-time.
- Ensure the system is kept up to date with the latest security patches and firmware updates.
By adhering to these guidelines and leveraging the WP500’s robust security features, users can establish a strong defense against network threats and maintain the security and integrity of their systems.